BYOD Part 1: Enterprise Strategy and Policy
Bring Your Own Device (BYOD) refers to an organization-led program which permits employees to bring personally owned mobile devices (laptops, tablets, and smart phones) to their workplace, and to use those devices to access privileged company information and applications. It is a known enterprise mobile strategy which has gained acceptance in numerous markets:
• Corporate: BYOD is fast becoming standard practice in the corporate world. More companies are allowing employees to utilize their own personal mobile devices to access the network for communication and collaboration, wireless presenting, file download and share and more. By employing a structured BYOD program, including policy implementation, enterprise companies can maintain enhanced BYOD management. Third party mobile device, application and content management as well as targeted security solutions can further enhance strategy in terms of securing devices, apps as well as critical files and data (especially when lost or misplaced) which are accessed with these personal devices (Note: this will be further defined in part two of this series).
• Healthcare: Mobility is improving patient care and operational efficiency. In hospitals and clinics, along with a provider using their own device, multiple medical professionals can also share the same device as well. Because of the sensitivity of healthcare data, the device must always remain under management with enforced security policies even between users. Requirements in terms of policy enforcement as well as conforming to HIPAA standards are paramount when healthcare professionals utilize their own devices. Device, app and data security are paramount to any healthcare BYOD program.
• Government: In Federal, state and local government, mobile devices are taking an employee’s work and communications on the road with them. Emergency workers can be in touch at any time as well as see information and data anywhere they are. Securing sensitive files and data is critical in this market as well as implementing and enforcing a strong BYOD policy. As in healthcare, device, app and data security become paramount to any BYOD program. BYOD programs have been developing in more of a measured approach in the Federal market, however it is gaining certain popularity in terms of an organization’s mobile strategy.
• Higher Education: The BYOD movement had its start in colleges and universities nearly a decade ago, spurred on by technology-savvy students who requested to use their personal devices on campus and by forward-thinking administrators who recognized that allowing network access using personal devices could improve the educational experience while aiding their recruiting efforts as well. This strategy has grown exponentially in today’s education market with executives and administrators continuously developing and deploying BYOD strategies as well as coinciding policy.
The strategy, as versus utilization of organization-distributed devices as stated permits an employee to bring a personally owned mobile device (laptop, tablet, and smart phone) to their workplace, and to use that device to access certain company privileged information and apps developed by the organization as well. It can be deployed as a measure in certain cases for example to reduce costs, have employees use their own resident applications (i.e. Linkedin, Twitter) resident on their device along with downloaded organizational apps (based on permissions established for each employee). However the program, most importantly, allows for an employees to use their own familiar native devices.
Here is an infographic which shows today’s enterprise market BYOD trends:
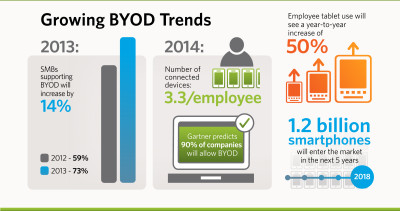
A recent ZDNet article Bring-your-own-device gains traction in the U.S. — even if enterprises aren’t ready yet, begins with a summary statement: Gartner says about two-fifths of all U.S. consumers who work for large enterprises use their own device for work. With BYOD gaining further acceptance in enterprise markets, however, come inherent risks as well. If there is little management and control, numerous things can happen to compromise the organization.
However with the implementation of a BYOD program, one important thing that needs to be established (as noted in the market sector descriptions above), is a clear and concise BYOD policy. BYOD program management and enforcement concerning employee usage of and network access with these devices by an organization’s IT department should coincide with an established policy that is signed off by all employees involved in a BYOD program.
The following is a video “Consumerization of IT in the Enterprise: Bring Your Own Device (BYOD)” (part of a four-part series on the Consumerization of IT).
CIO Steve Phillips of Avnet Inc.,.one of the largest distributors of electronic components, IT solutions and embedded technology, shares his key considerations when developing a Bring Your Own Device (BYOD) policy in the enterprise, including how Avnet’s own policy is evolving.
The following are some considerations for drafting a strategic BYOD policy:
- Will there be an agreement put in place for employees that wish to bring their own devices?
- What regulations, if any (government, industry, or otherwise), must be adhered to when an employee uses their own device?
- Will you specify which types of devices (brands, OS) that employees can use within the organization?
- Who will pay for the devices and data coverage required — individual, organization or both?
- What privacies will be granted to employees using their own devices?
- What support (software updates, troubleshooting, maintenance, etc) will the organization provide for BYOD users?
- What measures (e.g. software installation, enterprise mobile management) will be taken for securing devices prior to use?
- What methods will be used for securing devices when lost or stolen?
- Are there safeguards in place if a device is compromised?
- Is there a plan for retiring employee devices when they leave the organization?
- What happens if an employee violates BYOD policy agreement
Once a policy has been created, maintaining BYOD management and security depends on an organization’s ability to educate its employees on BYOD best practices, implement effective mobile management and security measures, and enforce the policy. Employees that are not trained on BYOD policy procedures will only increase management and security risks for the organization. An outdated policy can also lead to management issues. Therefore, creating a sound and strategic BYOD program, as well as continuously updating one that is already in place are imperative and must be undertaken in a collaborative and concerted effort between an organization’s employees, IT team and management.
Avoiding BYOD? Why Setting BYOD Policies is Increasingly Critical





