Cybersecurity Lessons Learned from Zoom, Logitech and Draper

Photo by Irvan Smith
By Paul Konikowski, CTS-D
Last week was a big week for cybersecurity news pertaining to the audiovisual industry.
Vulnerabilities in Zoom’s Mac desktop client were disclosed, hijacking flaws in Logitech’s Unifying USB dongles hit the mainstream and Draper, Inc. announced that its computer systems and communications networks were being held hostage by ransomware. Let’s take a closer look at each news story, and see what lessons can be learned from them.
Webcam and DoS zero-day vulnerabilities uncovered in Zoom Communications’ Mac desktop client
This Zoom vulnerability is bananas. I tried one of the proof of concept links and got connected to three other randos also freaking out about it in real time. https://t.co/w7JKHk8nZy pic.twitter.com/arOE6DbQaf
— Matt Haughey is at OSCON this week (@mathowie) July 9, 2019
Zoom Video Communications provides software that offers cloud-based video conferencing, online collaboration, webinars,and digital signage. Last Mon., July 8, 2019, cybersecurity researcher Jonathan Leitschuh publicly disclosed details about a vulnerability he discovered in Zoom’s client for Apple Mac computers, which could allow a malicious attacker to hijack users’ webcams by simply sending them a link that would automatically launch a video conference call. This vulnerability was actually more of a feature that Zoom built into their Mac client so that users would not need to click an extra button to join a Zoom meeting. Leitschuh also explained that attackers could launch a denial-of-service (DoS) attack on Mac users using the same vulnerability to overwhelm their computer networks with requests to join a meeting. The DoS attack vulnerability was patched in client version 4.4.2 back in May, but the webcam vulnerability remained until Zoom started to feel the heat on Twitter and other social platforms earlier last week. Cybersecurity experts slammed Zoom for not taking the vulnerability threat seriously, not being more responsive to Leitschuh’s repeated communications to them about it and for publicly discrediting his research work on social media:
“I also recommend that any researcher that finds a vulnerability in Zoom’s software does not directly report the vulnerability to Zoom. Instead, I recommend that researchers report these vulnerabilities via @thezdi (ZDI)”
When vuln disclosure goes wrong, researchers go elsewhere https://t.co/DPztP98uzh
— Katie Moussouris (@k8em0) July 9, 2019

Photo by Tayyab Ejaz
Until last week, the Zoom installer would set up a local web server on the user’s Mac that allowed Zoom call URLs to automatically launch the Zoom desktop app, working around the extra click required by Safari 12. According to a statement issued by Zoom Monday night, “The local web server enables users to avoid this extra click before joining every meeting. We feel that this is a legitimate solution to a poor user experience problem, enabling our users to have faster, one-click-to-join meetings. We are not alone among video conferencing providers in implementing this solution.”
Even after a user uninstalled the Zoom client, the web server remained, and Zoom stated: “The user needs to manually locate and delete those two apps.”
By Tuesday morning, Zoom started to sing a different tune. CEO Eric Yuan hosted a party chat with Leitschuh and other interested individuals, took their concerns seriously and escalated the issue. Zoom released a patch later that day that completely removed the local web server once the Mac client was updated. They also added a new option to the Zoom toolbar that allowed users to manually uninstall Zoom.
The conversation with the @zoom_us CEO in the ‘Party Chat’ was incredibly productive. It felt like an about face on their previous position on this #vulnerability. It’s really encouraging to see a CEO willing to jump into a call with a bunch of strangers to take responsibility.
— Jonathan Leitschuh (@JLLeitschuh) July 9, 2019
On Wed., July 10, 2019, Apple issued an update to its Mac operating system that completely killed off the Zoom web server, just in case Mac users did not update their Zoom client software on their own. Zoom promised a planned release for the weekend of July 13, which would address the video-on-by-default setting in the Zoom client. The full timeline and updated statement in this blog post from Zoom CEO Eric Yuan. This morning, I was on a Zoom call and at the end was asked to update my software. In addition to the planned updates mentioned above, it also turned off the feature that used to automatically start the video when joining a call.
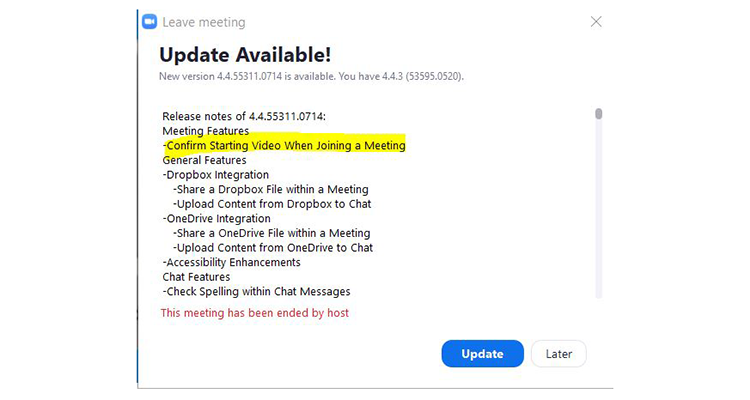
Lessons learned from the Zoom zero-day vulnerabilities
The only way Zoom will get back public confidence is:
1) Issue a public apology. Admit fault completely, with no excuses.
2) Pay the bounty for the researchers work, and apologise for discrediting his work on social media.
3) Commit to independent security audits.— Mike (@mikebull) July 10, 2019
The first lesson to be learned from the Zoom news is that equipment manufacturers and software providers need to be responsive to researchers when vulnerabilities are discovered and reward them. Zoom offered Leitschuh a bug bounty, but only if he agreed to sign a non-disclosure agreement, which he declined, because he felt that the public disclosure was more important than the cash that they offered. They should also offer a public apology and commit to having independent third-party security audits, as indicated in the tweet above.
The other big lesson is that oftentimes, making the user experience easier is often a direct tradeoff for security. The principle of psychological acceptability was outlined along with other secure design principles in a 1975 IEEE paper by Jerome H. Saltzer and Michael D. Schroeder titled The Protection of Information in Computer Systems, which states: “It is essential that the human interface be designed for ease of use, so that users routinely and automatically apply the protection mechanisms correctly.”
In other words, make the systems easy to use, but without sacrificing the necessary security protections. Settings like auto-join should not be on by default and hidden in a settings page. If a user chooses to uninstall the software, it should be a complete uninstall; don’t make them hunt around for a rogue web server.
Vulnerabilities discovered in Logitech’s Unifying USB dongles
On the same day that the Zoom vulnerability news hit, ZDnet and other mainstream IT media websites reported on multiple flaws in Logitech’s Unifying USB dongle that were uncovered by researcher Marcus Mengs. According to the article and the corresponding entries in the NIST National Vulnerability Database, the flaws allow nearby attackers (within 10 meters) to steal the AES encryption keys used when pairing wireless keyboards, mice and presentation clickers with the USB dongle. With these keys, attackers can decrypt the keyboard data stream remotely, capture keystrokes, including passwords and even inject arbitrary keystrokes. The first flaw was actually discovered and patched in 2016, and involved transmitting RF packets to a Logitech Unifying dongle, bypassing the encryption. The more recent flaws discovered allow an attacker to steal the encryption keys and capture keystrokes in addition to injecting them. Mengs originally started tweeting about the recently discovered vulnerabilities back in May and has since developed his own dongle called LogiTacker to test for the vulnerability. (Test meaning you can easily accomplish the hack yourself using the LogiTacker device). Alpha testers have confirmed it works. Mengs released the details of his research this past Thurs., July 11, 2019.
Because of arising discussion, due to media releases on Logitech research, I decided to publish the related content today (raw documents, vendor reports, slide deck from talk, PoC tools).
LOGITacker will be released on Thursday.https://t.co/FPEks2NKky
— Marcus Mengs (@mame82) July 9, 2019
What does a wireless USB dongle have to do with integrated AV systems?
Audiovisual integrators often incorporate so-called room PCs or Mac computers into conference room AV systems and provide Logitech wireless keyboards and mice so that users can control the rack-mounted computers from any seat at the conference room table. If a malicious attacker simply unplugs the Logitech dongle and plugs it back, he or she can capture the encryption keys and log keystrokes from any of the users. So if an organization’s IT department policies forces users to type their own unique login credentials every time they use the room PC (a good practice called complete mediation), the malicious actor can capture the login and passwords if he or she is within range of the Logitech wireless dongle. AV integrators should use this as an opportunity to contact their existing customers and let them know about the security flaws.
Lessons learned from the Logitech USB Dongle flaws
The biggest takeaway from the Logitech news is that wireless devices are never as secure as hardwired connections. By their nature, they broadcast their signals and anyone within range of the broadcast can intercept the transmission. As shown with the Logitech Unifying USB dongle vulnerabilities, even encrypted signals can be hacked. Wired systems can also be hacked, but wireless systems are generally more vulnerable, because wired systems usually require an intruder to physically intercept the signals. There are ways to spy on wired signals without physically interrupting them, but it is not an easy task.
The other lesson learned is that not all vulnerabilities can be fixed with a simple software patch or firmware update. As I mentioned, one of the vulnerabilities was discovered and patched back in 2016. Logitech plans to patch one of the three new vulnerabilities in August, but has no plans to patch the other two. The company recommends that, “a computer (with a USB receiver) should always be kept where strangers cannot physically access or manipulate it. In addition, users should take common security measures to make it more difficult for others to access it.”
So the only thing users can do right now about their vulnerable Logitech USB devices is lock them in a secure AV rack (you know, the ones with common keys) or throw them into the trash. But, if you want to keep your Logitech devices and update the firmware to address some of the vulnerabilities (to patch the 2016 flaw now, and then again in August, to patch one of the three new flaws), you can download the Unifying software to view the firmware version here and download the firmware update tool SecureDFU here.
Draper, Inc. suffers ransomware attack, taking down their computers and many communications channels
Last but not least, Draper, Inc. announced late on Wed., July 10, 2019 that its systems had been infected by ransomware. According to the announcement on Twitter, “[Draper’s] communication and computer systems have been encrypted by ransomware. Draper will continue to be closed on Thursday, and is not manufacturing, shipping, or entering orders.”
They also told customers to: “not open any attachment or click any link sent from an email address at draperinc.com.”
The banner at the top of their website still indicated that their communications systems were still not functioning properly:

The latest update at the time of publication of this article indicates that the company has regained a small amount of control — limited email communication is back, as well as very limited manufacturing, they are shipping out some orders on a limited basis and Draper’s main website at draperinc.com is back up (the window shade ordering website at draperonline.com is not back yet). The phone systems are still down and the company is still not accepting new orders. See the latest update here.
Draper has been in business since 1902, before most Americans had electricity in their homes. It initially manufactured window shades for schools. In 1957, Draper patented an inexpensive projection screen and over time, has become a massive producer of screens and related projection equipment. In 1989, it entered the gymnasium market, and currently manufactures and distributes basketball backstops, gym dividers, wall pads, volleyball equipment, batting cages and wrestling mat hoists. Draper still make shades. With U.S.- and Europe-based manufacturing, Draper products are shipped to over 100 countries.
One hundred and seventeen years in business. Thousands of customers in over 100 countries. Imagine the financial data that could be stored on their servers, which may or may not have been breached; no indication of a personal data breach or business data breach have been released at this time. Employee health data is also a big concern — Draper has its own employee health clinic! Not to mention the impact of just a couple days without business communications.
Lessons learned from the Draper ransomware attack
The first lesson learned from the Draper ransomware attack is to have an incident response plan in place, so all employees know exactly what to do, and what not to, in the event of a cyber-attack. Draper’s immediate communication about this attack was handled very well.
Second, consider paying the ransom if you are infected with ransomware. Studies have shown that most ransomware attackers will uphold their side of the deal and will unlock the data once the ransom has been paid. If attackers just kept the money and the data stayed locked up, then no one would ever pay the ransoms. If you can’t confidently restore your systems back to normal within 24 hours, chances are that you will spend more money trying to fix your systems than the original ransom — not to mention the cost of lost business because your employees can’t process orders, answer emails, etc. A good example of this is 2018 cyberattack on the city of Atlanta, which affected utilities, parking and court services. The attackers, who were later indicted, demanded $51,000 in Bitcoin as their ransom. The city chose to not pay the ransom and instead spent millions of dollars rebuilding their systems. Draper has not said if it is going to pay the ransom.
I applaud Draper for its transparency and professional disclosure of this ransomware attack and encourage other AV manufacturers to do the same when they suffer a similar ransomware attack or data breach. Notice I said when, not if. It’s simply a matter of time until every single manufacturer, integrator and distributor in the AV business gets hacked. Some have probably already been attacked and either didn’t disclose the details (pre-GDPR regulations), or they have no idea their systems have been breached. This means you!
Where do we go, where do we go now, where do we go (Sweet Child O’ Mine)?
I personally believe, or at least I hope, that this week will mark the “watershed” moment in audiovisual industry cybersecurity. Over the last few years, there have been a handful of security vulnerabilities discovered in touch panels, wireless presentation systems, video conferencing codecs, digital billboard signage players and other devices. But this week is different; moreover, the Draper ransomware attack is different. Unlike security vulnerabilities in devices and software that can be downplayed, patched and/or swept under the rug by manufacturers, data breaches are governed by laws like the EU’s General Data Protection Regulation, or GDPR. According to GDPR Article 33:
“In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay.”
The full details of GDPR Article 33 can be found here and should be considered with Article 34:
“When the personal data breach is likely to result in a high risk to the rights and freedoms of natural persons, the controller shall communicate the personal data breach to the data subject without undue delay.”
The full details of Article 34 can be found here. Anyone who does business with EU citizens or processes their personal data is subject to GDPR. There are also laws per different U.S. states.
Again, let me be clear that Draper has not confirmed any personal data breach.
But the mere chance of a data breach this large should make Draper and other AV companies realize how bad it could be. The impact of the Draper ransomware attack should make other AV companies realize they too are at risk, both financially and via reputation. By 2020, nearly everyone in the AV industry should be talking about cybersecurity, data privacy and ransomware. Or maybe I am wrong and everyone will continue to think cybersecurity is someone else’s problem and that cyberattacks will never happen to them.
For more information about the zero-day vulnerabilities mentioned in this article, please see the following entries in the NIST National Vulnerability Database:
Zoom:
CVE-2019-13449
CVE-2019-13450
Logitech:
CVE-2016-10761
CVE-2019-13052
CVE-2019-13054
CVE-2019-13055
 Paul Konikowski, CTS-D, is an independent freelance AV consultant and integration engineer. Paul earned his Bachelor of Science degree in computer engineering from Georgia Tech. In 2018, Paul completed Harvard University’s online shortcourse, “Cybersecurity: Managing Risk in The Information Age,” and is now pursuing a Master of Science degree in cybersecurity at Georgia Tech. He can be reached via Twitter at @PKaudiovisual or via email pkav.info@gmail.com.
Paul Konikowski, CTS-D, is an independent freelance AV consultant and integration engineer. Paul earned his Bachelor of Science degree in computer engineering from Georgia Tech. In 2018, Paul completed Harvard University’s online shortcourse, “Cybersecurity: Managing Risk in The Information Age,” and is now pursuing a Master of Science degree in cybersecurity at Georgia Tech. He can be reached via Twitter at @PKaudiovisual or via email pkav.info@gmail.com.




