Security Through Light: The World’s First Quantum Secured Video Conference
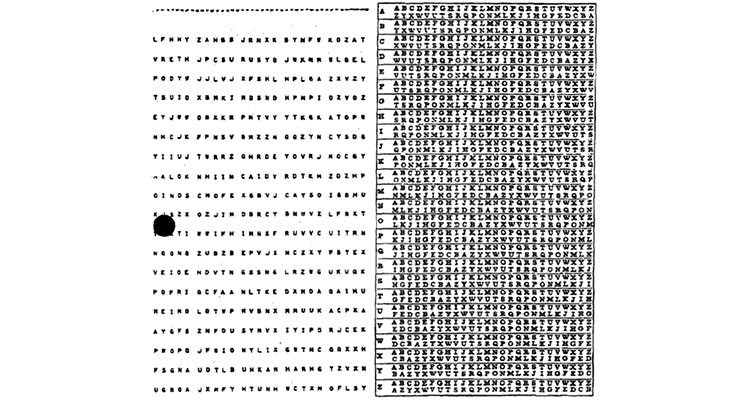
A format of one-time pad used by the U.S. National Security Agency, code named DIANA. The table on the right is an aid for converting between plaintext and ciphertext using the characters at left as the key. Image via Wikipedia.
My readers will know that I tend to focus on topics related to collaboration, user-interaction, and generally building products that help us work together. You may be surprised to learn that a significant amount of my time is spent thinking about security. As devices become increasingly attached to our enterprise networks – those same devices must be secure, good citizens of the network infrastructure.
Even products that were once considered “standalone,” for example most AV hardware, are connected to the network for better monitoring, ease-of-use and pervasive access for users. As an aside, if you are considering deploying an AV technology you should be wary of standalone boxes, and even more wary of AV companies that seem reluctant to discuss network security with your security teams.
As I monitor the NIST database—an ongoing security research project—and think about security for our own products, I was pleasantly surprised to see that Quantum Computing has found its first killer application – an unbreakable approach to secure communication. “Unbreakable? Impossible!” I know it may seem that way, but that’s because we’ve gotten used to thinking about encryption using our current “public key” techniques. Bear with me, let’s quickly review how encryption (at a high level) works today.
Fundamentally encryption requires us to agree on the encryption algorithm (the key). But to do this we have to first exchange the key. If the key is stolen, then our subsequent communication is insecure. Picture us meeting in an alley and whispering “increment every third letter by the next one in the alphabet.” In the mid-1970s computer scientists looked at this and derived a way to avoid sending the key in the open but still keep the algorithm secure. These encryption algorithms rely on the fact that some mathematical operations are straightforward to compute but very difficult to invert. For example, multiplying two very large prime numbers is simple, but discovering the two primes that were used to create a large number can be very difficult. Modern encryption algorithms rely on this fact to exchange a “public” key that, when used with the prime numbers that made it, lead to the encryption cipher. To derive the private algorithm from the public key requires huge computational energy and unrealistic amounts of time.
Almost all secure communications rely on these algorithms. As secure as they are, they can be broken. Here is an important fact: Even the most secure cipher that uses public key algorithms (RSA, Diffie-Hellman, and ECC) can be broken. It can take a very long time, but as long as you have enough computing power it can be done. In fact, given the rate at which computing advances, one could imagine storing today’s communication until such time computing power reaches a point at which you could then decrypt the world’s communications.
In 1977, probably the most cited paper on public key cryptography appeared in Scientific American. In that article, it was estimated that it would take 40 quadrillion years to decrypt a message encoded with the RSA-129 cipher (based on how long it would take to factor the 2^129 bit number into the two hidden primes). That’s a long time. However, 20 years later, networked, parallel computing was developed, and that cipher was cracked in less than six months.
So, what do I mean by an uncrackable code? Forget the issue of exchanging the encryption algorithm itself for a minute. What would be the most secure cipher? It turns out, it’s probably the one you used as a kid to send messages to your friends: The One-Time Pad. It’s really a character-by-character agreed upon replacement algorithm. (Swap every third letter with the next one in the alphabet). Here’s how it works. For any message length, I will combine that message’s characters with a secret set of characters that are at least as long as the message. Character-by-character I combine the secret “pad” with the message itself using simple modulus arithmetic. Why is this so secure? Because the pad is the same length and generated each time a new message is exchanged – breaking this code would be equivalent to guessing the pad – which is, of course, equivalent to guessing the message itself. The number of possible messages in a string of characters of any reasonable length is so large that it would take longer than 40 quadrillion years to simply guess – and even if you guessed correctly, there’s no way to be sure you have the correct message.
One-time pad ciphers have been used in the past, but their weakness is susceptibility if the pad itself is stolen. While the technique might work for sending a single encrypted message, hand your friend the one-time pad and she’ll know how to decrypt the next letter she receives in the mail. It’s clearly not valuable for micro banking transactions over the internet.
The problem is in how do you send the one-time-pad securely? This is what quantum computing can give us. On September 29th, researchers utilized Quantum Key Distribution (QKD) to secure a video call between Austria and China. The “one-time-pad” in this case was a secret string of numbers that were to be used to encrypt the incoming video call. I won’t go into the physical/mathematical explanation of quantum entanglement, but, the one-time-pad is sent via light through a fiber optic cable. Small quanta of light (photons) are governed by quantum mechanics and, in that tiny world, measurements always disturb the system in a way that can be detected. Measure the position of an electron, for example, and you’ve in part, changed the system behavior. This is true for even passive observations.
This means we can happily exchange a one-time pad via a quantum communications channel and then check if the pad was observed at all. If it was not, both parties can go ahead and use the pad knowing it’s secure. Even better, it’s not susceptible to even theoretical cracks via computational techniques like public-key methods are today.
Pretty awesome. This historic call involved chemist Chunli Bai, president of the Chinese Academy of Sciences in Beijing, and quantum physicist Anton Zeilinger, president of the Austrian Academy of Sciences in Vienna. Rupert Ursin, a member of the Vienna research team was rightly excited and was quoted as saying, “We are facing, now, a new era of having a global quantum internet ready to be deployed.”
It will be a while before you can buy a quantum-secured Solstice Pod, but, nonetheless, it does make one think about how rapidly these technologies will arrive in the real world.





