BYOD Part 3: Your *Own* Device Realities
BYOD: The practice of allowing the employees of an organization to use their own computers, smartphones, or other devices for work purposes. It is part of the larger trend of the consumerization of IT.
When seeing a product called a “BYOD box” I have to wonder just how you put box at the end of this statement. When referencing a “BYOD collaboration” solution, is this an application that works just within this definition? Can company-owned devices work? Can a CYOD program (choose your own device) which is gaining popularity in organizations fit within the scheme as well?
Some things to note which could make one begin to change thought process concerning BYOD in AV. Certain technology trends start the same way: cause a revolution, be a (pick a buzz word). disrupt the industry and beyond. X might somewhat change the form and function of the company, as well as the lives of some people who work there.
And so goes the BYOD movement where it seems to be great advantage to the organization to have their employees use their own laptops, tablets and smart phones instead of having to buy those devices and maintaining the hardware and infrastructure to support it. With cloud-based systems and strategies, this should seemingly be a no-brainer. The organization saves money, and employees would use what they love. The best of all worlds?
Maybe not.
In a recent CIO article BYOD – the tech revolution that wasn’t, according to a study by IT industry trade association CompTIA, companies are moving away from BYOD as a primary device method, be it as part of a full or partial program. An online survey conducted in April and May of 375 U.S. IT professionals in various private businesses found that 53 percent allowed no BYOD, up significantly from 34% in 2013.
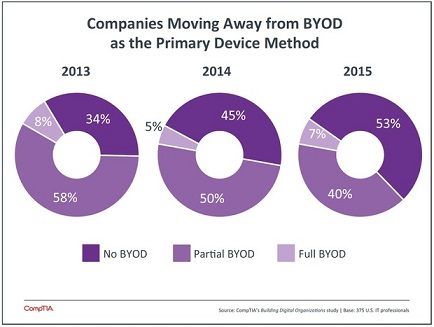
No BYOD represents an organization that provides smartphones and tablets to workers and bans the use of personal devices for work, which could potentially be considered a “non-native” device for an employee if an Android phone user is given an iPhone for business usage (or even a different type of Android phone). Partial BYOD, the organization provides some devices but allows some personal devices to access corporate systems. Where the aforementioned CYOD (Choose Your Own Device) is concerned, according to the report where there is a further movement towards no BYOD, companies find they can pursue mobility initatives just as well by providing mobile devices to workers “who are often happy to take a corporate device if it is the same thing they would choose on their own.” It’s been suggested to possibly consider this the corporatization of the consumerization of IT.
When still considering BYOD in the enterprise where it applies as organizational strategy, implementation leading to setting proper BYOD policy in place becomes the basis of what can be considered a successful program. Proper BYOD policy would include listing approved (and possibly unapproved) devices, requiring complex passwords, full understanding of service policy, approved apps for business usage (which may exist in a corporate app store), and having an effective employee exit strategy. An employee signs documentation which spells out this policy.
While the enterprise to a certain degree has been able to implement BYOD programs for business process, it’s believed that IT departments are still lagging where policy is concerned, as percentages can still be considered somewhat deficient. One report from CIO|Insight in May specified that only 34 percent of those surveyed stated that their employer has a BYOD policy in place.* According to the previously mentioned CIO article, Erika Van Noort, senior director of strategic customer enablement at Softchoice states that “It’s not the rapid expansion into this area that it was a couple of years ago,” and that “the [companies] that really wanted to go there went there quickly.” Where policy is concerned, Van Noort also claimed how “A lot of companies don’t actually think through the policy” as she alluded to how many jumped in fast to implement a program when BYOD was introduced.
However for those who do have BYOD programs and set proper BYOD policy, everything is good — right?
With sign off on BYOD policy, the employee is then placed within the organization’s security chain. If the employee does not keep their own devices up-to-date and patched, chooses to use open and less secure Wi-Fi networks for business transaction or communication, or uses unapproved applications including public cloud storage services to share and store corporate documents, there is little that a company can do to enforce basic security protocols — putting networks and sensitive data at potential risk.
A ZDNet article – BYOD employees ‘indifferent’ to enterprise security claims a new study reveals that the next generation of workers is placing the enterprise at risk with a lax attitude toward mobile security. A striking statement from the article: Businesses are ill-prepared for the attitude of next generation employees who own mobile devices, and may be placed at risk as the BYOD trend causes fractures in security enforcement.
Ben Gibson, CMO of network access control provider Aruba Networks states:
“These trends underline that #GenMobile employees continue to be a growing part of the everyday workforce, but they also bring with them some risky behaviors. In a contemporary connected world, firms need to nurture creativity, while at the same time minimize the risk of data and information loss.
As a result, employers need to take an adaptive trust approach to connectivity and data security, identifying individual worker preferences that factor multiple layers of contextual information in order to build secure infrastructures around them.”
Renee Guttmann, vice president, information risk in Optiv‘s Office of the CISO in Denver, Colo. stated “The trend toward mobilizing enterprise-critical systems and data adds to concerns over BYOD security.” **
As the enterprise faces certain realities in terms of the current state of BYOD strategy and implementation, it’s apparent that the BYOD that the industry talks about may truthfully be considered a part of what is considered more of a “mobile first” revolution in the enterprise world (as is referenced in Microsoft’s Mobile First, Cloud First mantra). Bring Your Own Device may just translate to Bring Your Own Mobile Strategy — not that that should become an acronym anytime soon…
* IT Departments Are Lagging on BYOD Policies (slideshow)
** Is BYOD policy the foundation for mastering enterprise mobility?
ZDNet article: BYOD employees ‘indifferent’ to enterprise security







