Securing AV: The SolarWinds Attack of 2020 (Actually 2019)
For each column in this series, rAVe writer Paul Konikowski takes a deeper dive into a recent security event or data breach, shedding light on supply chain vulnerabilities, infrastructure, and cyber-physical security.
While most Americans are still processing the recent attack on the United States Capitol building, many cybersecurity researchers and professionals believe the real war began online back in 2020. Some are calling it the “cyberpandemic” as forewarned just six months before at the 2020 World Economic Forum.
solarwinds123
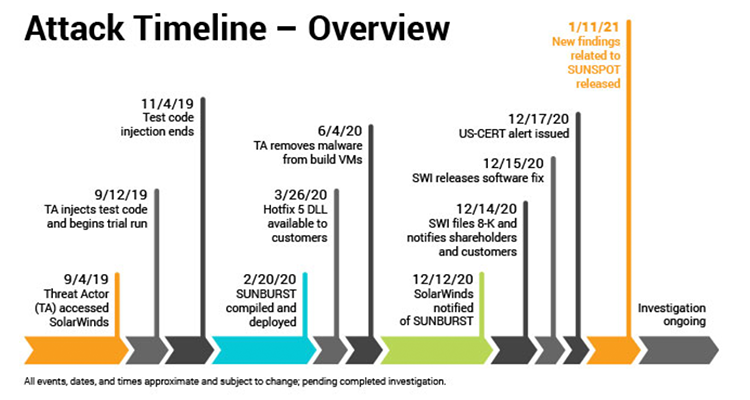
According to a recent report from Crowdstrike, this so-called cyberpandemic actually started back in September 2019 (the good old days) when a group of hackers first breached the network of an American software company called SolarWinds. (Some sources, including the Washington Post, identify Russia-based Cozy Bear as the hacker group behind the breach.)
Once the hackers gained access, likely by guessing the password, “solarwinds123”, they went to work inserting batch number one of malicious code, known as Sunspot, into the SolarWinds build server. (A build server is a type of software used by developers to assemble smaller software components.) Sunspot was designed to wait for a build of the SolarWinds Orion software — then inject a second malicious payload program, called Sunburst, into the SolarWinds Orion software package.
The problem gets considerably bigger when one thinks about how widely popular SolarWinds Orion is. The Orion software package is an IT resource monitoring package used by over 33,000 organizations, including the United States Federal Government, other governments, and many Fortune 500 companies.
Therefore, when clients installed the SolarWinds Orion software update, they also installed malicious Sunburst. Sunburst then collected data and sent it back to the hackers using DNS requests, as detailed by Symantec.
The threat actors (hackers) cleaned up after themselves to some degree, and removed the malware from the SolarWinds build servers a few months after the malicious software update had been delivered. Another six months went by with the infected code on tens of thousands of IT networks — including the government servers — before anyone noticed.
Here is a timeline of the attack as provided by SolarWinds:
Where Does Microsoft Fit In?
Microsoft was one of the SolarWinds customers who was attacked in what they call, “Solorigate,” which included the previously mentioned Sunburst payload, but also a number of other attack methods. This was not just a single-door attack, this was a multiprong, long-term, advanced persistent threat.
Way back in 2019, I wrote an article about the then proposed MICROCHIPS Act, and I warned readers:
“There could be scenarios in which malware could implanted into legitimate software updates, either the software production level, or by a third-party vendor. Source code could be added to firmware updates to take advantage of zero-day vulnerabilities and back doors in chips. Don’t think your AV system will be targeted? Just consider how many of today’s AV devices have network jacks on them.”
The SolarWinds attack did exactly that; it used a legitimate software update process to distribute itself. Microsoft explains and expands deeply on this subject in its blog post:
“The addition of a few benign-looking lines of code into a single DLL file spelled a serious threat to organizations using the affected product, a widely used IT administration software used across verticals, including government and the security industry. The discreet malicious codes inserted into the DLL called a backdoor composed of almost 4,000 lines of code that allowed the threat actor behind the attack to operate unfettered in compromised networks … The fact that the compromised file is digitally signed suggests the attackers were able to access the company’s software development or distribution pipeline. Evidence suggests that as early as October 2019, these attackers have been testing their ability to insert code by adding empty classes.”
This is the main takeaway in my opinion: Every time you issue an update, you may be issuing malware.
There is a lot more to the Microsoft analysis, and the APT attack, and lot more “big takeaways” emerging from the “lessons learned” memos. Alex Weinert, the director of identity security at Microsoft, suggests a zero-trust approach to network traffic, which “assumes breach and explicitly verifies the security status of identity, endpoint, network, and other resources based on all available signals and data.”
So, where do we go from here? First, we should expect a spike in data breaches and ransomware attacks because there are still thousands of companies who have not realized their networks are compromised. This will go hand-in-hand with the elevated tensions from extremists and militant groups, who are now resolute on reforming the U.S. government, and have also been told that Big Tech is part of the problem.
And if the extremists think that Big Tech is part of the problem, are we not in danger as technologists? It’s important not to jump to extreme conclusions, for extreme thinking leads to extreme situations. At the same time, we need to understand and appreciate the gravity of the SolarWinds/Solorigate cyberattack, and to keep in mind that something as simple as good password hygiene can help prevent a massive cyberattack. Also, think twice before you issue a software update; you may also be spreading malware.





