#HootHoot Meeting Owls Security Vulnerabilities Have Been Patched, Have Yours?

“Owl Labs product,” by Matthew Stein, licensed under CC BY-SA 4.0, resized from original.
In January 2022, cybersecurity researchers at Modzero reported a handful of security vulnerabilities to Owl Labs regarding their 360-degree videoconferencing Meeting Owl, Meeting Owl Pro, Meeting Owl 3, and Whiteboard Owl. Owl Labs has since released patches for these vulnerabilities.
(The below is the Meeting Owl 3, as shown at InfoComm 2022.)
The security patches were issued soon after the researchers publicly released the 40-page vulnerability report on May 31, 2022, along with a shorter summary post. Ars Technica also reported the story in June 2022, (essentially five months after the vulnerabilities were reported).
As an industry, we need to do better. Not just in our quickness in responding to security concerns, but in general. I will expand on that more later in this article. First, let’s talk about the associated CVEs.
What’s a CVE?
CVE is short for Common Vulnerabilities and Exposures, a list of exploits maintained and verified by MITRE. Each “vuln” gets a unique CVE ID number which includes the year. Here are the four CVEs associated with the Owl Labs Meeting Owls.
- CVE-2022-31459 — allows attackers to retrieve the passcode hash over Bluetooth.
- CVE-2022-31460 — allows attackers to activate Tethering Mode with hard-coded “hoothoot” credentials. The result is a rogue wireless access point that routes all network traffic through the Owl to the LAN.
- CVE-2022-31461 — allows attackers to deactivate the passcode protection mechanism.
- CVE-2022-31462 — allows attackers to control the device via a backdoor password (derived from the serial number) that can be found in Bluetooth broadcast data.
- CVE-2022-31463 — does not require a password for Bluetooth commands, because only client-side authentication is used.
Let me put all of this together in a hypothetical story, highlighting how each vulnerability could be exploited:
Let’s pretend a small town uses a Meeting Owl to help broadcast their town hall or utility board meetings. The Meeting Owl sits on the town’s LAN/WAN, which is shared with some other servers.
A hypothetical malicious attacker attends a local council budget meeting, or simply sits outside the door within range of the Bluetooth and Wi-Fi. The attacker connects to the Meeting Owl via Bluetooth (because authentication only happens on the app, not on the Meeting Owl (CVE-2022-31463)).
The would-be attacker uses information broadcasted via Bluetooth to figure out the device’s serial default password, which is the SHA-1 encrypted version of the serial number (CVE-2022-31462). SHA-1 can be easily decrypted. If Wi-Fi has been disabled, the attackers can turn it back on using Bluetooth.
Once connected to the device, the bad actor can turn off all password protection (CVE-2022-31461). The hard-coded backdoor passcode “hoothoot” allows them to put the device into Tethering mode. (CVE-2022-31460). This creates an access point where all network traffic is automatically routed to the LAN.
“No big deal. The attacker needs to be close to the device to hack into it, right? So as long as the hackers don’t know where the Meeting Owls are physically used, we are okay, right?”
Using the serial number, the Modzero researchers found they could retrieve the details of the Meeting Owl end users that were stored in a database hosted on the internet. No password was required to access the database. Instead, all the researchers needed was a valid Meeting Owl serial number. Subsequently, the security researchers wrote a program that tried every possible serial number (which is only made up of numerical digits); this is also known as a brute force break-in. The server responded with personal details including location information for every Owl that had been registered. Using this information Modzero created a map of some of the Meeting Owls, as depicted below.
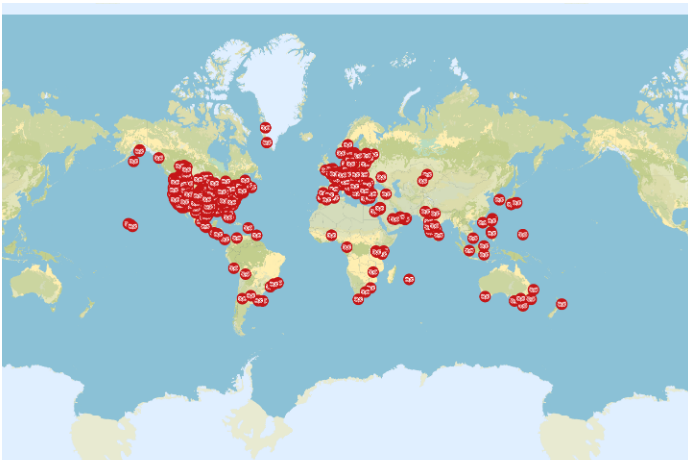
Real Meeting Owl locations (Source: https://modzero.com/modlog/archives/2022/05/31/en_hoot_hoot_pwn/index.html)
Lessons Learned From the Vulnerabilities and Security Patches
Let’s start with Bluetooth and a related story: About a year ago, I was speaking with an audio product representative who was talking about a new wireless microphone system. The new platform would allow AV engineers to adjust the settings on the wireless microphone channels, including gain and mute on/off, using only a Bluetooth-enabled smartphone. I asked the product rep if anyone within range of the Bluetooth could maliciously mute the microphones during a performance. They admitted this scenario was possible because the authentication was only on the client-side of the app. Sound familiar? The Meeting Owl had the same vulnerability! So, the first lesson is don’t design Bluetooth smartphone apps with client-side only authentication. Assume a hacker will use the app and Bluetooth to attack the device. And then, limit how much functionality is available via Bluetooth. Least Privilege!
Lesson two: Whenever someone touts the Bluetooth capability of a new device, you should immediately ask about security. “Can the Bluetooth functionality be turned off completely?” A great question to start with. Ask what happens when a malicious hacker connects to the device.
Third lesson: If you are a manufacturer and you are alerted to a problem, don’t wait to fix it. Respond immediately to the researchers who reported it. Issue a patch within 90 days, six months maximum. It’s mind-blowing how many manufacturers make this same mistake. They initially ignore the emails and phone calls. When they finally get back to the researchers, they say it’s no big deal; others will say the product is end-of-life and there is no record of anyone exploiting the vulnerability “in the wild.” Some will eventually issue security patches (like Owl Labs did, THANK YOU) while others sit on their hands.
Last tip: (and I can’t believe I have to say this, but) Please don’t host an online database of end user information/locations that can be easily accessed using plain serial numbers. Think, people!
We NEED to do better. We can NOT keep installing The Colonel’s Secret Recipe of Audiovisual Products, hoping they communicate over others’ networks, and running away when we get everything “talking.”
We cannot leave the cybersecurity of networked AV devices up to the local network administrators.
We need to take ownership of all AV device security if we are going to sell and install those same AV devices. It is not illegal to install an unsecured audiovisual system, but maybe it should be. Maybe if audiovisual integrators were held liable for installing nonsecure AV systems, for not configuring them correctly or enabling logging for attribution, they might take the AV device security more seriously.
Here is a link to the latest security update from Owl Labs as of July 22, 2022.
The Meeting Owl Pro will automatically send over the air updates to Owls that are connected to Wi-fi and plugged in overnight. Here is the support page for more information.
On July 1, 2022, a full month after the vulnerability disclosure, Owl Labs published this webpage: “Were my Owls affected by the recent security findings?” Note how the company took full credit for identifying the vulnerabilities, announcing them to the users, and “promptly began to roll out security patches.”