The Ongoing “New” Prospects for Security in AV

How the “New” industry security discussion really began
Back in mid-January of this year, the AV world was rocked by a story that truly caught fire within hours after it was first reported. I watched it filter through the industry – the articles and podcasts – however I waited for the right moment to post my blog “Baffling” Backdoor Cyber-Talks as the facts (and fiction) continued on for days in and outside the industry. That in itself is another story. It was no mistake that baffling was put in quotes as the title referred to an article written by Forbes/ Security’s Thomas Fox-Brewster (@iblametom) “Baffling ‘Batman’ Backdoor Busted In Comms Used By Global Governments”, as he pulled the trigger the morning of January 21st on a story he was well aware was taking place through his already formed connection with Austrian firm SEC Consult.
Along with this came the conversation which no doubt led to one of the more misunderstood events in the history of the AV industry, with reports akin to the White House being under apparent siege by hackers through AMX equipment installed on the network, and thus AMX would be in grave trouble over this. Shall I say in both cases, this wasn’t the case. Yes, AMX was somewhat negligent and admittedly so, however there was no presence of a breach reported at the White House, nor any branches of Federal government or military that utilize installed AMX equipment. This was in no way close to the Juniper/NSA backdoor incident as was referred to in the Fox-Brewster article, as others were latching on to as well.
I wrote a follow-up to this one called Security and the AV Industry – Time to Expand on Message, Perspectives and Awareness where I had stated how industry, long based in on-premise security solutions was now looking hard, with the AMX incident still fresh ink on the presses, at a security discussion crossroad. I also pointed out in the blog that I had the opportunity to discuss this with a leader in the AV Industry who is also deeply involved in IoT and cybersecurity, Gary Hall, CTS-D, CTS-I, Chief Technology Officer for Federal Defense at Cisco Systems. This is a portion of Gary’s statement:
“The need for better cyber security is absolutely critical to the success of digitization efforts that include human to human communications and decision making processes that are facilitated by professional AV systems. The rise of IoT and continued growth in collaboration and communications has created tremendous opportunities to unlock new value in all types of businesses, but they also create new risks that must be mitigated.”
Some facts behind this new industry security discussion
It’s a given that technology – IT, AV, IoT – continues to evolve at a rapid pace, and the frequency and level of cyber-crime activity is evolving right alongside it. AV-Test, an Independent IT-Security Institute, claims that 390,000 pieces of new malware are found every day — over 270 per minute. Financial as well as revenge-motivated cyber-criminals increasingly have the tools at their disposal to craft treacherous, targeted attacks. The mantra repeated endlessly is it’s more likely a case of not if, but -when- your organization is going to suffer a damaging breach.
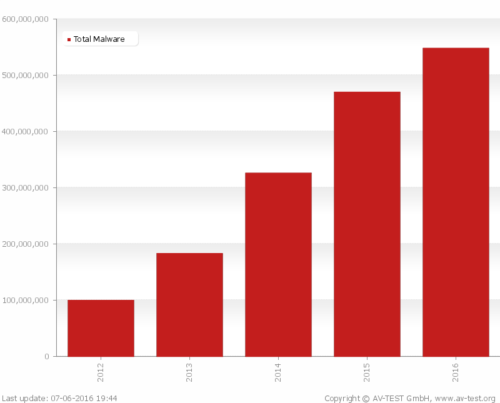
Total malware last 5 years according to AV-Test study – last updated 7/6/16.
Research by Ponemon Institute* has shown that the biggest problem facing an organization’s security today is the negligent or careless employee with multiple mobile devices using commercial cloud apps and working outside of the office. It’s been reported that most organizations that have experienced a data breach has taken place due to insider threat, and much of it actually comes down to staff being uneducated on cybersecurity and its importance. Where the ongoing discussion of mobile device usage is concerned, which at times includes BYOD as a buzz-term, there needs to be a potential focus on security discussion as well. The industry should actually discuss these as mobile or mobile device solutions and applications, not BYOD – to be more in line with most enterprise mobility initiatives.
Where the security discussion needs to be driven on an industry level
If there is indeed real discussion of BYOD on an enterprise level, one must be mindful of the security discussion that should follow along. There are numerous excellent resources for this – here is one from Symantec. When talking with the CIO, or if by chance you meet with the CSO – make sure you have that discussion ready if necessary. Even if it’s the tech manager, a basic knowledge of security discussion can potentially mean the difference in winning a trusted partnership. When working on any proposal which involves networked AV and/or mobile device usage, security must also play a role in the planning and implementation.
On the subject of networked AV and security, this has been discussion that has been a part of the industry for some time, however I see it as potentially hotter now than it’s ever been. Paul Zielie of Harman, well-known as the industry’s expert, discusses the topic at numerous events and trade shows in the industry. I consider this video presentation as one that should be required viewing for all in the industry involved in AV and networking – and if you have the opportunity to attend a presentation given by Paul in person, I would say capitalize on it. His sessions as he’s told me are never exactly alike, so you may get varied important information in any one that you may attend.
Note: This is the preview video – a link to the complete video presentation can be found in the description on YouTube.
Back in April, I noticed this post on Twitter from industry integrator Synergy CT about the development of an AV security checklist, which links to an excellent blog (that includes reference to the AMX incident) detailing Why You Should Focus on AV Security:
Develop a systematic approach to network #security with our AV Security Checklist! https://t.co/fkKKB8gkzE #AVTweeps pic.twitter.com/dknSrDRHUv
— Synergy CT (@Synergy_CT) April 29, 2016
Can the industry gain expertise in the near future to the extent that the tech manager and CIO (and possibly the CSO) will be able to leverage an AV integrator’s knowledge-base and solutions offerings in security as well? More to come on the discussion of network, mobile and cyber security (to include IoT) in the AV industry.
* 2015 State of the Endpoint Report: User-Centric Risk – an annual study conducted by Ponemon Institute to understand trends and changes in endpoint risk in organizations.
Forbes/ Security: Baffling ‘Batman’ Backdoor Busted In Comms Used By Global Governments